
Doosra: Protecting your mobile number
Submitted Sep 1, 2022
Summary
Doosra provides an alternative virtual number to the primary phone number to protect our privacy. In today’s interconnected world, we share our mobile number everywhere, and in return receive unwarranted messages and calls. Doosra provides a platform that gives the user control to allow or restrict access. The entire solution has been designed keeping privacy at the core.
The process to obtain a Doosra number is simple and quick, and this can be done using the website or the mobile App. KYC and e-KYC need to be completed by the user as required by law. A unique user ID is then assigned to every user which is used throughout the system. Even the SMSes are encrypted with unique encryption keys for each user. All the content is visible only to the user on the mobile App.
The Doosra implementation follows industry best practices. Only minimal user data is collected and is stored securely in the servers to be compliant with telecom regulations. Access control is restricted based on individuals and their roles. AWS Firewall and the use of API rate limiters help prevent DDoS attacks. AWS CloudTrail is setup for logging, tracing and audits. In future, Doosra plans to pseudo-anonymise all Personal Identifiable Information (PII) so that no application can have direct access to the data.
Introduction
Doosra provides a virtual mobile number as an alternative to the primary phone number to protect our privacy. We often give our mobile numbers at malls, shops, and websites, and receive spam via calls and messages. The Doosra platform acts as a gateway to your mobile number, and gives you control to allow or restrict access. The entire solution has been designed keeping privacy in mind while also being compliant with telecom regulations.
Problem Statement
The mobile number serves as our digital identity in today’s highly interconnected world. The phone number is a mandatory requirement for nearly every important service - banking, ecommerce, Aadhaar linking, 2FA etc. Even social media platforms allow login using a mobile number. Realistically, sharing the number is only a necessity in certain situations like an ecommerce purchase that requires physical delivery. But, even if the transaction is not digital, the mobile number is asked in a brick-and-mortar setup.
The sharing of the mobile number has a number of problems, and we are seeing a rising number of fraudulent cases. We receive prank calls, scam calls [1], feedback calls, and incessant follow-ups from service providers. We also receive marketing and promotional messages from unwarranted sources. These add to the cognitive overload that we already face in this highly connected world. There is significant research that points to a direct correlation between smartphone usage and cognitive decline [2]. Phone and OS manufacturers themselves have introduced mental wellness features such as Zen Mode, Do Not Disturb (DND), and Night Mode to help their users live a better life.
A simple example of SMS Phishing [3] by clicking a link from an SMS can leave our phone compromised, enabling the perpetrator to gain access to critical information like your name, date-of-birth, address etc. This data can be used to engage in activities like SIM Swap Frauds [4] and enables fraudsters to access your social media and bank accounts. The Aadhaar information can be obtained quite easily via an OTP verification on the relevant UIDAI website or approved mobile application. The problem is further aggravated when this compromised data is shared between multiple parties. Moreover, with this personal information, attackers can also bypass security questions and even get a new SIM issued to them after which they can access anything that needs an OTP. While OTP as an authentication mechanism is quite robust and safe, it is no longer sufficient.
While consumers are aware of these issues, they are also left with little or no choice, since the mobile number is mandated at most places.
Software Architecture
Doosra offers an alternate mobile number to its users for an upfront fee and this number can be shared everywhere. A mobile App interface is provided to manage the number where every call is blocked by default. The phone numbers that are whitelisted alone can reach the user, and the call is forwarded to the primary mobile number. Even then the primary number is unknown to the caller. SMSes can be read on the mobile App or can be left untouched based on the user’s preference. Notifications are again consent-based, and users can give out their Doosra number, switch off their App notifications and forget about receiving any unwarranted calls or message notifications. It is not easy to trace back to the user’s primary mobile number. These are the many ways by which users can gradually take back control of their privacy.
Design Principles
Data Retention and Disposal Strategy
The data policy at Doosra is to only collect the data that is critical to providing optimal service and for complying with regulations. This is why the data collected from the user is kept to a minimum as shown below:
| Data Type | Stage | If Mandatory? | What is this data used for after completing signup? |
|---|---|---|---|
| Primary Mobile Number | Signup | Yes | Forward calls to users who choose to receive them |
| Signup | No | An optional and occasional update about Doosra or newsletter. | |
| KYC Document | e-KYC | Yes | Nothing. It’s stored securely for regulatory purposes. |
| User Activity | Post-Signup | NA | Allow the user to access the messages, calls, and voicemails that they receive on their Doosra number |
Once a user’s account expires (if not renewed), all of the user’s data is purged 18 months from the date of their account expiry i.e. the users’ calls, messages, voicemails, and KYC data are deleted from our servers completely. Only certain high-level metadata is retained for legal compliance.
Data Security
SMSes are encrypted with unique encryption keys for each user. The payments are processed via Razorpay, and hence payment details such as bank information and credit card information are not stored on the company servers. The minimal user data that is collected is stored securely in the Doosra platform. No individual in the company can view end user activity like SMS content and, any system-level access is used to fetch only metrics at an aggregation level. Also, any feature in the mobile App that requires extra permissions is completely consent-based. Here is a list of important permissions that are required from a data security standpoint:
| Permission | Mandatory |
|---|---|
| Camera | One-time Access for KYC |
| Storage and Media | One-time Access for KYC |
| Network & WiFi State | Yes |
| Location | No (only if the feature is used) |
Access Control
The accesses to source code repositories and databases are restricted based on the developer’s role. All developer and administrator accesses are logged and tracked for auditing purposes. AWS CloudTrail is used to monitor and record account activity across the AWS infrastructure. AWS Firewalls are used as a primary layer of protection to help monitor, track and prevent malicious requests, and block attacks on systems. The company’s ethos on the collection and usage of user data is reflected in their privacy policy.
Rate limiters
All important APIs have rate limiters enabled that ensure that the number of requests coming through in a given period of time are monitored and blocked as appropriate. This plays a pivotal role in preventing DDoS attacks. The accounts with repeated login attempts are locked, and they can only be unlocked after the support team verifies the authenticity of the user. While login to a Doosra account is via OTP only, having a rate limiter provides an additional layer of protection for user accounts.
User Activity Data
As a user continues to use the Doosra platform, their messages, calls and voicemails continue to accumulate in the system. The message body is encrypted as soon as it lands on Doosra servers, and the plain text version is only visible to the end-user via the mobile App. Other data, while not encrypted is stored securely and is only accessible to the user through the mobile App.
Reference Implementation
The Doosra platform has been built with privacy at its core. The Doosra number is used instead of a user’s primary number and hence all the calls and SMSes land on the Doosra number. The message data is encrypted, using symmetric data encryption algorithms, as soon as it reaches Doosra’s servers, and the decrypted messages can only be seen by the user on their mobile App once they log in with their credentials. Nobody, even at Doosra, can read the unencrypted data.
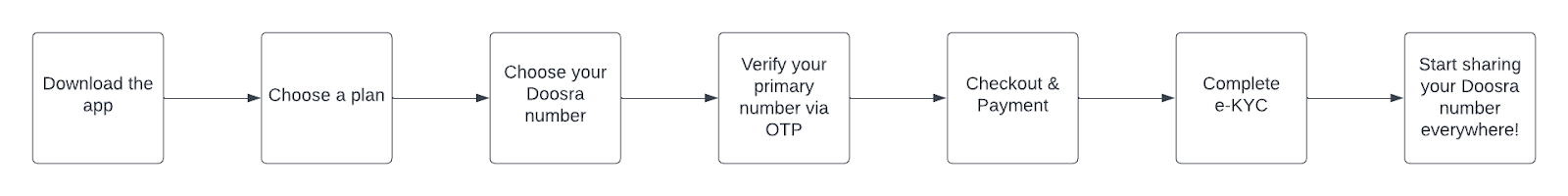
Subscribing to a Doosra number is a simple and quick process. A number can be selected and purchased within two minutes. Signup can be done either through the website or using a mobile App, available on both Android and iOS. A flowchart explaining the process to subscribe to a Doosra number on the App is shown below:
In order to be compliant with regulations, an OTP verification of the primary number and KYC verification of the user is done, but this data is unimportant after the verification stage. Users are also required to complete a mandatory eKYC process, as required by law. The data collected here is used solely to verify the authenticity of the user. At Doosra, the user product is the Doosra number and the mobile application.
After the signup process, the only identifier that Doosra has of the user is their primary mobile number used to verify the authenticity of the user. Another reason that Doosra needs the primary number is so that calls may be forwarded to this number. A unique User ID is then assigned to every user throughout the system - in the APIs, reports, and queries. This prevents the primary number from being exposed in any eventuality.
Conclusion
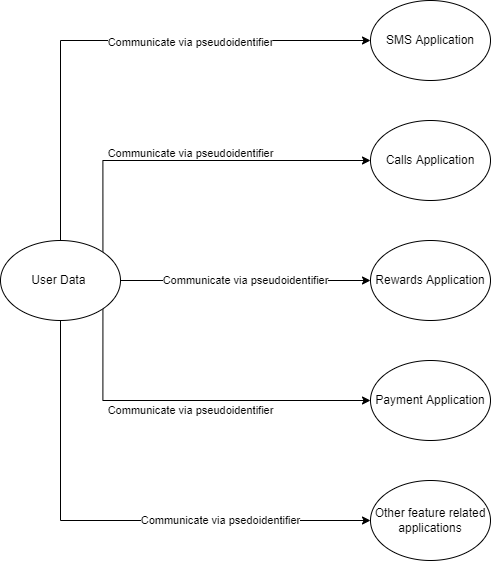
Doosra provides an additional layer of security by providing an alternate number to your phone. The entire design is centered around protecting the privacy of the user’s mobile number. A proposal exists to move in a direction that pseudo-anonymised all Personally Identifiable Information (PII). This essentially means that even applications within Doosra will work with pseudo-identifiers as user IDs instead of using the present user ID setup. No application (like the SMS or calls applications) will have direct access to the PII data at any point in time. The Doosra platform provides a real world example of designing systems and services keeping privacy in mind.
References
-
Five common phone call scams and how to avoid them.
https://www.doosra.com/blog/5-common-phone-call-scams-and-how-to-avoid-them. -
Adrian F. Ward, Kristen Duke, Ayelet Gneezy, and Maarten
W. Bos. “Brain Drain: The Mere Presence of One’s Own Smartphone
Reduces Available Cognitive Capacity”.
https://www.journals.uchicago.edu/doi/full/10.1086/691462 -
What is Smishing and How to Defend Against it.
https://www.kaspersky.com/resource-center/threats/what-is-smishing-and-how-to-defend-against-it -
Beware of SIM Swap Fraud.
https://www.hdfcbank.com/personal/useful-links/security/beware-of-fraud/sim-swap
Comments
Hosted by
Deep dives into privacy and security, and understanding needs of the Indian tech ecosystem through guides, research, collaboration, events and conferences. Sponsors: Privacy Mode’s programmes are sponsored by:
more
Supported by



{{ gettext('Login to leave a comment') }}
{{ gettext('Post a comment…') }}{{ errorMsg }}
{{ gettext('No comments posted yet') }}