Digital and information infrastructures are the new business layers to interact with consumers as part of regulatory requirements. How secure are these systems? How do businesses connect with these infrastructures to provide over-the-top services to citizens/consumers/users?
FifthElephant introduces a new project about the application of consent and crypto-based principles for tech platforms and products. This project includes:
- Explainer sessions.
- AMAs with practitioners who work on platforms.
- Call for Presentations (CfP) to showcase application of consent and crypto-based practices in the industry and government.
- Fostering collaborations within the business and engineering communities to work towards mitigating the risks associated with information infrastructures.
The first session under this project is an in-depth explainer about consent and how crypto brings proof and enables trust. The Digital Locker system allows businesses to fetch KYC documents using the electonic consent architecture. The electronic consent architecture is deemed as the digital standard by Ministry of Electronics and Information Technology (MEITY) for all the upcoming information architectures and data exchange platforms.
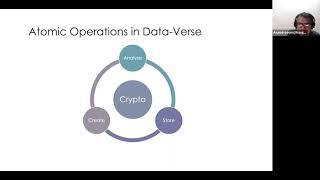
This session will help engineers, product managers and business heads to comprehend how digital architectures need to be designed. Anand Venkatanarayan will explain the concepts of informational theory and cryptography are applied in real world digital infrastrcutures. He will talk about how consent works for digital lockers infrastructures and how crypto enables trust showcasing Amazon S3 as a casestudy. He will also point to other crypto based principles like differential privacy and how crypto helps achieve privacy.
Slides for this talk are published on: https://www.slideshare.net/AnandVenkatanarayana/consent-crypto-and-information-infrastructure-systems-234711563
Who should participate:
- Engineers and product managers who work on integrating consent frameworks in their products.
- Business professionals who want to understand risks of information infrastructures.
- InfoSec and security practitioners.
- Crypto practitioners and researchers.
Pre-event comments and questions should be posted on https://hasgeek.com/fifthelephant/security-verifiability-and-the-business-of-information-infrastructures/comments
**Participation is via Zoom. The link to join the call is ** https://zoom.us/j/94367728721?pwd=R1hLTlFHalU2c0Z2ZEMyTlY3OVR4dz09
References for this session:
- Electronic Consent Framework
- Digital Locker Technology Framework
- Digital Locker Authority
- Differential Privacy for Non Technical Audience
About the organizers: The Fifth Elephant is platform for practitioners working with data (engineering, to application of data science for different use cases) to showcase their work and to collaborate.
For further inquiries, contact 7676332020 or write to fifthelephant.editorial@hasgeek.com